When a guest hands over their passport at check-in, they’re not just completing a booking, they’re entrusting you with data governed by global privacy laws impacting hospitality, across multiple jurisdictions, each with distinct requirements that could affect your operations.
Today’s hospitality leaders face a complex landscape of global privacy laws that demands strategic attention across multiple regions, each with unique requirements that fundamentally impact hospitality operations worldwide.
Understanding these critical jurisdictions with their distinct approaches to data protection, shared liability risks, and enforcement mechanisms, is essential for hospitality success in today’s interconnected and increasingly privacy-conscious world.
The Global Privacy Landscape: Critical Laws You Need to Know
The New Global Reality
The modern privacy regulatory environment has evolved far beyond any single framework. While GDPR established the foundational principles that influenced worldwide legislation, regional laws now add critical requirements that create a complex compliance matrix. Privacy laws worldwide are creating coordinated enforcement power, exemplified by the 7-state US regulator consortium that formed in 2025, bringing federal-level coordination to state privacy enforcement.
Each jurisdiction takes a unique approach to data protection and guest rights, from Europe’s comprehensive framework to India’s consent-centric model to China’s strict localization requirements. The Asia-Pacific region is emerging as the fastest-changing and most diverse regulatory landscape, with countries like India implementing entirely new frameworks that challenge traditional compliance approaches. The regulatory environment has never been more complex, or more consequential.
Why This Matters for Hospitality
Guest verification requirements vary dramatically by jurisdiction, creating operational complexity for multi-location operators. Cross-border data flows face different approval mechanisms globally – what works for European operations may violate Chinese or Indian requirements. Multi-jurisdictional operations must account for overlapping regulatory frameworks where the same guest data may be subject to multiple, sometimes conflicting, legal requirements.
Your global technology stack must comply with the strictest applicable standard from any region where you operate or serve guests. This reality transforms vendor selection, data architecture decisions, and operational procedures from local considerations into global strategic imperatives.
For hospitality tech vendors, this complexity multiplies as your platform must enable compliance for clients operating across multiple jurisdictions. Your users rely on your technology infrastructure to handle these varying requirements seamlessly, making privacy compliance a critical competitive differentiator and client retention factor.

The Strategic Opportunity
The financial case for proactive compliance is compelling: The average cost of a data breach in the hospitality sector is around $3.4 million, while strategic privacy investments often deliver measurable returns. Organizations implementing jurisdiction-aware verification systems achieve up to 90% fraud reduction while building guest trust as a competitive differentiator in privacy-conscious global markets.
Forward-thinking hospitality leaders are discovering that privacy compliance, when approached strategically, drives operational excellence, enables confident market expansion, and creates sustainable competitive advantages in an increasingly data-driven industry.
The Big 5: Critical Jurisdictions You Can’t Ignore
1. European Union: GDPR – The Global Foundation

The General Data Protection Regulation (GDPR) applies to any organization processing EU residents’ data, regardless of location. It’s the global gold standard that established the modern privacy framework influencing regulations worldwide, with extraterritorial reach that makes it relevant for all international hotel chains.
Key Elements
- Six Lawful Bases for Processing
- Consent – Freely given, specific, informed, and unambiguous permission
- Contract – Necessary for booking fulfillment and service delivery
- Legal Obligation – Required by applicable laws and regulations
- Vital Interests – Protection of life in emergency situations
- Public Task – Government functions and public authority activities
- Legitimate Interests – Balanced against individual rights and freedoms
- Data Subject Rights
- Access – Right to know what personal data is being processed
- Rectification – Right to correct inaccurate or incomplete information
- Erasure – “Right to be forgotten” and data deletion
- Portability – Right to transfer data to other service providers
- Restriction – Right to limit specific processing activities
- Objection – Right to stop particular types of data processing
- Core Requirements
- Privacy by Design – Integration of data protection into all business processes and systems
- Data Protection Impact Assessments – Required for high-risk processing activities
- Cross-border Transfer Mechanisms – Adequacy decisions or Standard Contractual Clauses for data leaving the EU
Hospitality Screening & Verification Implications
Guest identity verification typically relies on “performance of contract” (booking) or “legal obligation” (local registration laws) as lawful basis. Joint controller liability under Article 26 affects multi-party operations where brands, operators, and owners share guest data responsibilities. Organizations must implement comprehensive Data Processing Agreements with all verification technology vendors. Guest consent for marketing use of verification data must be separate and withdrawable, requiring sophisticated consent management systems.
2. United States: The State-by-State Approach
No federal privacy law exists, but state laws like California’s CCPA/CPRA grant residents comprehensive rights over their personal information. Laws are now active in California, Virginia, Colorado, Connecticut, Utah, Texas, Oregon, Montana, and Delaware, creating a complex patchwork of requirements with varying thresholds and obligations.
Key Elements
- Four Fundamental Consumer Rights:
- Right to Know – Detailed disclosure of data collection, use, and sharing practices
- Right to Delete – Request deletion of personal information with limited exceptions
- Right to Correct – Request correction of inaccurate personal information
- Right to Opt-Out – Stop “sale” or “sharing” of personal data
- Broad “Sale” Definition:
- Beyond Monetary Payment – Includes sharing data for any valuable consideration
- Marketing Partnerships – Data sharing with advertising networks and analytics providers
- Loyalty Programs – Information exchange with program partners
- Third-Party Services – Sharing with vendors who provide insights or services in return
- Technical Requirements:
- Global Privacy Control (GPC) – Must honor browser-based opt-out signals automatically
- Automated Opt-Out Processing – Integration with website infrastructure required
- Ongoing Monitoring – Continuous compliance with automated requests
- Sensitive Personal Information Protection:
- Precise Geolocation Data – Requires explicit opt-in consent
- Health Information – Enhanced protection for medical and wellness data
- Biometric Identifiers – Strict consent requirements for biometric processing
- Other Specified Categories – Additional sensitive data types by jurisdiction
- Enforcement Evolution:
- Seven-State Regulator Consortium – Formed in April 2025 for coordinated enforcement (California, Colorado, Connecticut, Delaware, Indiana, New Jersey, and Oregon)
- Information Sharing – Joint investigations and consistent interpretation across states
- Federal-Level Impact – Coordinated state enforcement rivaling federal oversight
Hospitality Screening & Verification Implications
Identity verification data sharing with fraud prevention services may constitute “sale” requiring opt-out mechanisms. Geolocation data from mobile check-ins and health information for accessibility needs require explicit opt-in consent. Organizations must audit all verification vendor relationships for compliance with “Do Not Sell” requests. Automated decision-making in guest screening may trigger additional disclosure requirements, necessitating transparent algorithmic processing explanations.
3. India: DPDPA – The Consent-Centric Model
The Digital Personal Data Protection Act of 2023 applies to any organization processing Indian residents’ data with a strict consent-based framework that differs significantly from other global approaches. Unlike other laws, it operates almost exclusively on explicit consent without alternatives like “legitimate interest.”
Key Elements
- Consent Requirements:
- Four Critical Criteria – Must be free (no coercion/bundling), specific (clear purposes), informed (comprehensive disclosure), and unconditional (not tied to other agreements)
- Easy Withdrawal and Granular Options – Simple revocation processes with separate permissions for different processing purposes
- Processing Basis Limitations:
- Consent-Only Model – No “legitimate interest” basis available; virtually all processing requires explicit consent
- Limited Alternatives – Contract performance and legal obligation bases have very restricted scope
- Organizational Structure:
- Data Fiduciary vs. Processor – Clear accountability framework similar to GDPR controller/processor distinction
- Children’s Data Protection – Under 18 coverage requiring verifiable parental consent with ongoing management procedures
- Operational Requirements:
- Multi-Language Notices – Privacy notices must be available in 23 Indian languages with ongoing translation obligations
- Penalty Structure – Up to $30 million for serious violations with both regulatory and individual remedy pathways
Hospitality Screening & Verification Implications
All guest verification activities require explicit consent and cannot rely on contract performance or legal obligation. Family bookings with minors require verifiable parental consent for identity verification. Organizations must redesign verification flows to obtain separate consent for identity checks, fraud prevention, and any data sharing with verification vendors. Consent withdrawal must immediately stop all verification data processing, requiring real-time system capabilities.
4. China: PIPL – The Strictest Global Standard
The Personal Information Protection Law applies to organizations processing Chinese residents’ data and imposes some of the world’s most restrictive requirements, particularly for sensitive data and international transfers. It represents the most stringent approach to data protection globally.
Key Elements
- Separate Consent Requirements:
- Three Distinct Consents – Separate explicit consent required for sensitive data processing, third-party sharing, and cross-border transfers
- No Bundled Permissions – Each consent type must be obtained independently and clearly distinguished
- Data Localization and Infrastructure:
- Critical Infrastructure Operators – Large hospitality chains may face mandatory data localization requirements
- Domestic Storage Requirements – Personal information must be stored within China for qualifying organizations
- Processing Principles:
- Strict Purpose Limitation – Data use must align precisely with stated collection purposes
- Data Minimization Requirements – Collection and processing limited to what is necessary and proportionate
- Compliance and Oversight:
- Regular Compliance Audits – Personal information processors must conduct documented compliance assessments
- Government Approval Requirements – Cross-border transfers may require specific government authorization
Hospitality Screening & Verification Implications
Identity documents (passports, national IDs) qualify as sensitive data requiring separate explicit consent beyond booking agreements. Sharing verification data with international fraud prevention services requires additional consent and may need government approval. Large hotel chains may face data localization requirements, necessitating separate Chinese verification systems. Cross-border transfer of guest verification data faces significant restrictions and approval processes, potentially requiring local data storage and processing infrastructure.
5. Brazil: LGPD – The Flexible Framework
Lei Geral de Proteção de Dados (LGPD) applies to any organization processing Brazilian residents’ data, offering more processing bases than other laws but requiring mandatory local representation through Data Protection Officers. The law provides the most flexible global framework while maintaining strict accountability requirements.
Key Elements
- Processing Bases:
- Ten Lawful Bases – Most flexible globally, including consent, legitimate interest, contract performance, legal obligation, and six additional options
- Multiple Pathways – Greater operational flexibility compared to other major privacy laws
- Mandatory Organizational Requirements:
- Data Protection Officer – Required appointment for all covered entities with specific qualifications
- Local Representatives – ANPD now requires foreign companies to appoint Brazilian representatives for enforcement actions
- Rights and Transfers:
- GDPR-Similar Rights – Data subject rights mirror European provisions for access, correction, and deletion
- Cross-Border Safeguards – Transfers require adequacy decisions or specific protective measures
- Recent Enforcement Developments: Enhanced Local Presence – Foreign companies face increased requirements for Brazilian legal representation and compliance infrastructure
Hospitality Screening & Verification Implications
Guest identity verification can rely on multiple lawful bases including contract performance and legitimate interest for fraud prevention. However, foreign companies must appoint qualified Brazilian DPO and potentially local legal representatives. Verification data transfers outside Brazil require adequate safeguards through binding corporate rules or standard contractual clauses. Organizations must establish local incident response procedures for verification-related data breaches affecting Brazilian guests.
The Hidden Liability: Shared Responsibility in Hospitality Operations
The Problem
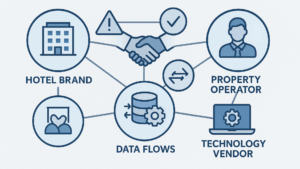
Property owners, operators, brands, and technology vendors often share data processing responsibilities in ways that create complex liability scenarios. Multiple parties may qualify as “data controllers” under different laws for the same guest data, while unclear liability allocation creates regulatory and financial exposure for all parties involved.
Common Scenarios
- Hotels: Brand controls loyalty programs and central reservations, operator manages property systems and guest interactions, owner handles local compliance and property-specific communications
- Short-Term Rentals: Platform manages bookings and payment processing, property manager handles operations and guest communications, owner controls direct guest relationships
- Technology Vendors: PMS providers, booking platforms, and verification services may be controllers or processors depending on specific data use and decision-making authority
Real-World Impact
Regulatory investigations can target multiple parties simultaneously, as demonstrated by recent GDPR enforcement actions against hotel chains where both brands and operators faced penalties. Data breach notifications may require coordination across several entities with different legal obligations and timelines. Insurance coverage gaps emerge when liability isn’t clearly defined in service agreements. Compliance costs multiply across shared responsibility chains, particularly when each party must maintain separate compliance programs.
Recommended Solutions
Organizations can significantly reduce their exposure to shared liability risks through several strategic approaches. Begin by conducting a comprehensive mapping of all data processing activities to clearly identify which parties serve as controllers versus processors in different scenarios. This analysis should inform updates to service agreements that explicitly allocate privacy responsibilities and establish appropriate indemnification frameworks.
Hotel Management Agreements and similar partnership contracts benefit from clear privacy liability allocation clauses that specify each party’s obligations for data protection, breach notification, and regulatory compliance. These contractual clarifications help prevent confusion during incidents and ensure that all parties understand their respective responsibilities.
Consider reviewing cyber liability insurance coverage across all entities in your ecosystem to ensure adequate protection for shared liability scenarios. Coordinated policy terms and coverage levels help eliminate gaps that could leave parties exposed during multi-entity incidents.
Finally, establishing coordinated incident response procedures creates a foundation for effective crisis management. These procedures should include clear communication protocols, responsibility matrices for different types of incidents, and streamlined processes for regulatory reporting that account for multi-jurisdictional requirements. Regular testing and updates ensure these procedures remain effective as business relationships and regulatory requirements evolve.
The Competitive Advantage Opportunity
Why This Matters Beyond Compliance
Guest Trust as Differentiator: In an era where data breaches make headlines weekly, transparent privacy practices become a powerful brand asset. Hotels and platforms that can demonstrate comprehensive privacy protection across all jurisdictions where they operate gain significant competitive advantages in customer acquisition and retention.
Operational Excellence: Privacy-compliant systems often drive better data quality, streamlined operations, and reduced manual processes. Organizations that implement privacy-by-design principles typically discover improved data accuracy, reduced redundancy, and more efficient guest service processes.
Market Access: Understanding regional privacy requirements enables confident expansion into new markets. Companies that proactively address privacy compliance can enter new jurisdictions faster and with less risk than competitors who must retrofit their operations.
Partnership Opportunities: Privacy-compliant platforms become essential infrastructure for brands operating internationally or serving global guests. Property management companies increasingly evaluate and select technology vendors based on comprehensive privacy compliance capabilities, viewing privacy-enabled platforms as strategic partners rather than replaceable tools. This shift enables privacy-compliant technology vendors to command premium pricing, secure longer contract terms, and win competitive deals against vendors who treat privacy as an afterthought.

The Strategic Shift
Organizations that view privacy laws as operational frameworks rather than restrictions often discover enhanced guest verification processes that reduce fraud while improving user experience. They achieve streamlined data management that eliminates redundancies and improves analytics quality. These companies build stronger vendor relationships based on clear data handling expectations and gain competitive positioning in privacy-conscious markets where regulatory compliance becomes a sales differentiator.
Industry Evolution: The hospitality sector is experiencing a fundamental shift where privacy-forward organizations gain sustainable advantages. Whether you’re a hotel chain expanding globally, a short-term rental platform entering new markets, or a technology vendor serving hospitality clients, understanding the global privacy landscape isn’t just about avoiding penalties—it’s about building the foundation for long-term success.
The Bottom Line: As privacy regulations continue to evolve and enforcement intensifies, organizations that proactively embrace comprehensive privacy frameworks will find themselves better positioned for growth, partnership opportunities, and guest trust in an increasingly competitive marketplace. The question isn’t whether to invest in privacy compliance, but how quickly you can transform regulatory requirements into competitive advantages that drive sustainable business growth.
This analysis represents current regulatory requirements as of January 2025. Privacy laws continue evolving rapidly, and organizations should consult qualified legal counsel for jurisdiction-specific compliance guidance.